
Defining Enterprise IT: Your Key to Digital Transformation
Defining Enterprise IT: Your Key to Digital Transformation Key Points Enterprise IT is the driving force behind businesses, providing a strong systems and services infrastructure[...]

How to Stay Safe After the LastPass Security Breach
In 2022, LastPass suffered a major cybersecurity incident, where hackers successfully breached their cloud infrastructure and obtained a copy of the password vault database.
Microsoft Sentinel vs. SentinelOne
Microsoft Sentinel vs. SentinelOne: What Are The Differences? Key Points: One is owned by Microsoft, while the other is a standalone solution by SentinelOne They[...]
Threat Actors Modified Zoom To Deliver Malware in a Phishing Campaign
Zoom Security Issues: Threat Actors Modified Zoom To Deliver Malware in a Phishing Campaign Key Points: Cybercriminals have launched a new malware to attack users[...]
How Long Does It Take A Hacker To Crack A Password?
How Long Does It Take A Hacker To Crack A Password? The time it takes for a hacker to crack a password can vary greatly[...]
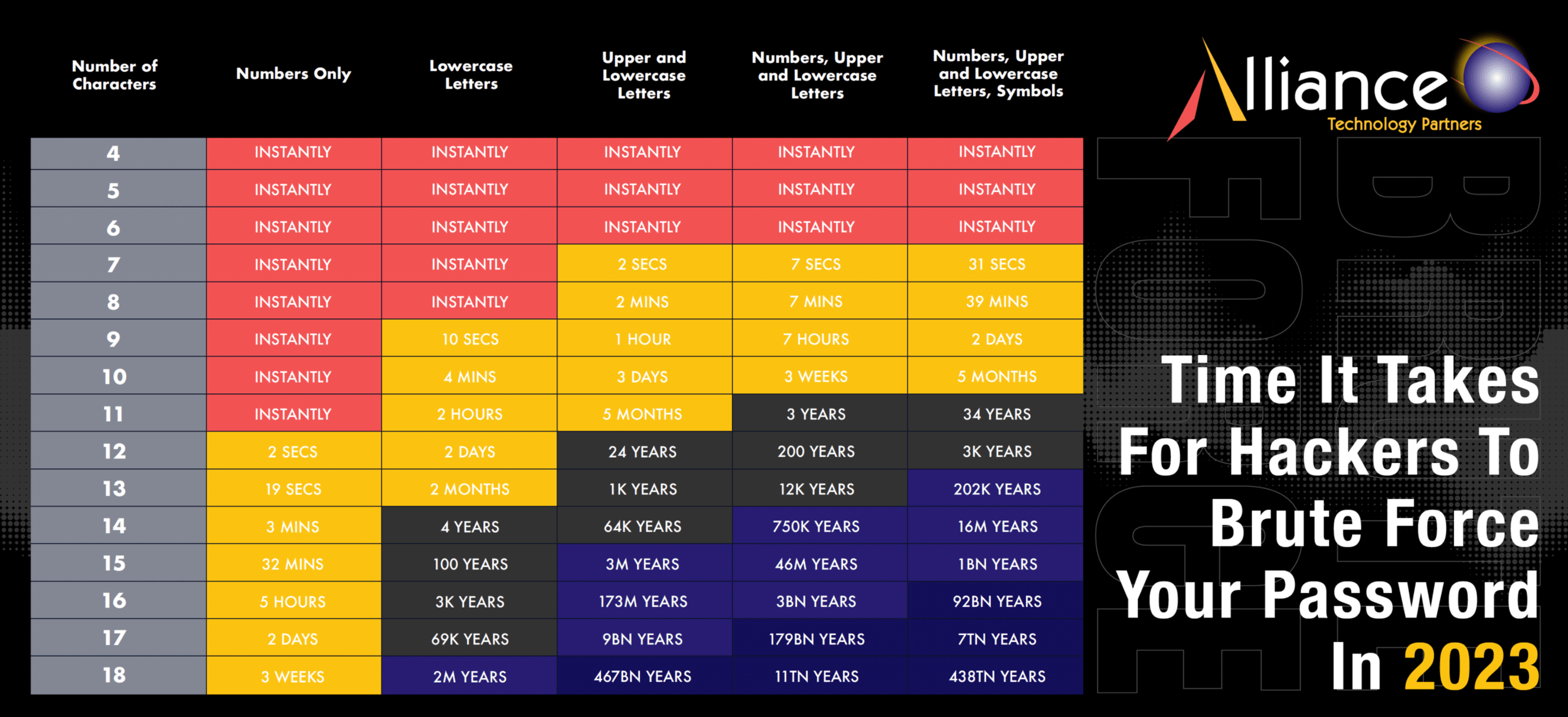
How Long Does It Take To Crack Your Password?
How long does it take a hacker to crack your password? Download this great cheat sheet from Alliance Tech Partners to find out.

FTC Extends Deadline for Revised Safeguards Rule Compliance to June 9, 2023
FTC Extends Deadline for Revised Safeguards Rule Compliance to June 9, 2023 Key Points The Federal Trade Commission (FTC) has granted an additional six months[...]
Hackers Don’t Discriminate
Hackers Don’t Discriminate: Worrisome Trends For Small Businesses Key points: More than 40% of cyberattacks target small companies. Since larger companies invest more money in[...]
How to Successfully Embark On Digital Transformation As A Non-Technical Business Owner
How to Successfully Embark On Digital Transformation As A Non-Technical Business Owner Key Points: Digital transformation is the top-of-mind leadership objective for many businesses. The[...]